As 6G promises unprecedented connectivity and ultra-low latency, researchers are tackling the formidable challenge of securing this high-speed, AI-powered network against advanced cyber threats with quantum-safe protocols.
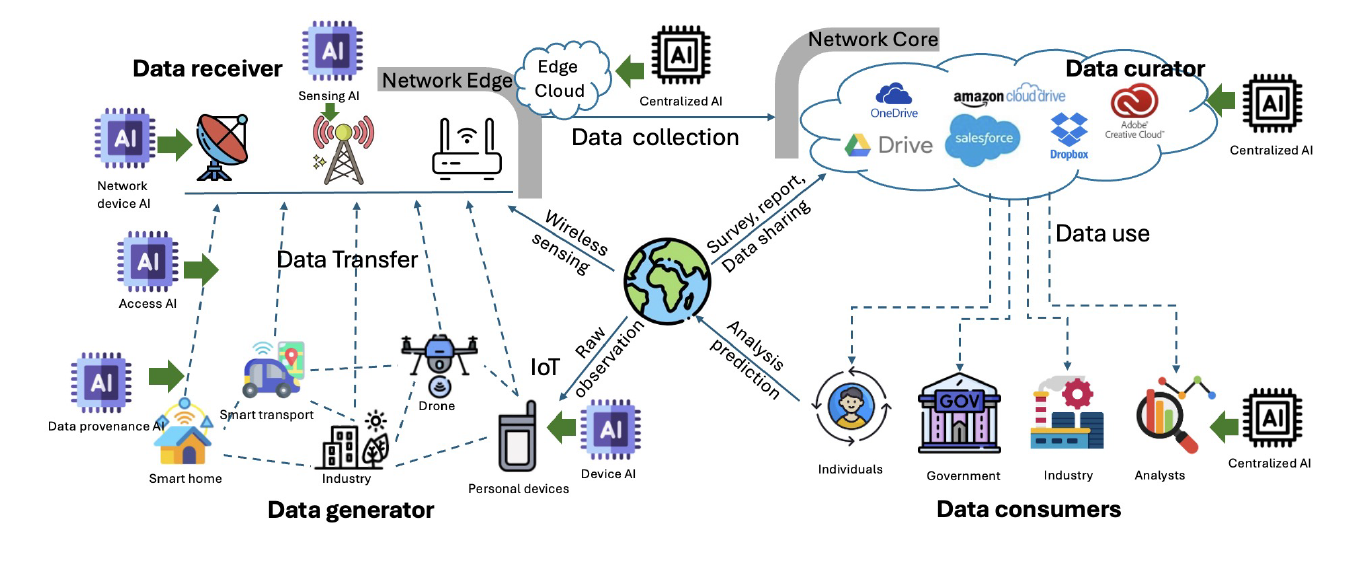
Data lifecycle in 6G environments. Research: From 5G to 6G: A Survey on Security, Privacy, and Standardization Pathways.

 *Important notice: arXiv publishes preliminary scientific reports that are not peer-reviewed and, therefore, should not be regarded as definitive, used to guide development decisions, or treated as established information in the field of artificial intelligence research.
*Important notice: arXiv publishes preliminary scientific reports that are not peer-reviewed and, therefore, should not be regarded as definitive, used to guide development decisions, or treated as established information in the field of artificial intelligence research.
In an article recently submitted to the arXiv preprint* server, researchers outlined the vision for 6G, highlighting advancements in data rates, low latency, and capacity to support immersive experiences and smart cities with artificial intelligence (AI)-driven network management.
They emphasized critical security and privacy challenges, including new threats from unauthorized access, data breaches, and evolving privacy risks in federated learning (FL) and multi-access edge computing (MEC) due to increased Internet of Things (IoT) and edge computing integration.
The paper reviewed 6G protocols and proposed specific mitigation strategies, advocating for "deep attestation" measures and enhanced customized solutions within current risk assessment frameworks.
Additionally, the study examined industry initiatives, government projects, and ongoing standardization efforts to ensure secure 6G deployment.
Quantum-Secure 6G Network Evolution
The evolution of mobile networks has shifted from simple analog systems in 1G to highly virtualized, cloud-native infrastructures envisioned for 6G, where programmability, deployment flexibility, and efficiency are prioritized.
Unlike previous generations, 6G architecture is expected to integrate quantum technology, enhancing security through quantum key distribution (QKD) and post-quantum cryptographic protocols like CRYSTALS-KYBER and CRYSTALS-DILITHIUM for robust resilience against quantum computing threats.
Key features include “network slicing” for adaptable, flexible service customization and AI-driven automation for real-time management. Legacy protocols such as Signaling System 7 (SS7), Diameter, and EAP will remain foundational, while post-quantum cryptography and proxy re-encryption techniques will address vulnerabilities posed by quantum computing.
With industry leaders' global investment in quantum technologies and advancements in secure quantum networks, 6G is geared towards robust and resilient connectivity in a secure post-quantum era.
Security Challenges in 6G Networks
6G networks face numerous security and privacy challenges from increased complexity, AI integration, and the deployment of novel technologies like quantum communications and holographic transmission. These challenges include existing risks such as distributed denial of service (DDoS) and falsified broadcasts, along with new threats like privacy risks in federated learning (FL) and multi-access edge computing (MEC).
Additionally, regulatory compliance for data privacy is critical, especially in international data transfers. Security mechanisms must ensure the isolation of essential services and proactively monitor shared infrastructure vulnerabilities, using frameworks like deep attestation to maintain trust and prevent resource exhaustion.
To improve 5G network security, operators monitor traffic, although encryption complicates the detection of malicious activity. In 5G, IPsec enhances data security between the radio access network (RAN) and the core. However, encrypted representational state transfer (REST) application programming interfaces (APIs) introduce risks, including malware and DDoS attacks.
Multiple probes in 5G networks, AI-based monitoring, and trusted execution environments (TEEs) help detect threats. Analytics tools monitor mobile threats, supporting attack detection and prevention. Frameworks like the European Union (EU) 5G security toolbox provide structured risk management approaches, while tools like the European Union Agency for Cybersecurity's (ENISA) data processing guidance help SMEs protect personal data.
Advancing 6G Technology Collaboration
Major industrial players like Nokia, Ericsson, Do Communications Over the Mobile Network (DOCOMO), Samsung, InterDigital, and Qualcomm drive 6G technology, focusing on ultra-high-speed communication, low latency, and AI integration.
This convergence of physical and digital worlds presents significant opportunities and challenges, particularly regarding data security and privacy.
Companies are investing in research and partnerships to advance 6G, emphasizing innovative applications across various sectors while addressing the heightened risks associated with increased connectivity and data collection.
Samsung Research is leading efforts in 6G technology, focusing on advanced antenna systems and intelligent networking. Establishing a new 6G research group in the UK in October 2022 marks a significant expansion of its global initiative. InterDigital is also actively engaged in 6G research and development, receiving funding for five projects under the 6G Flagship program.
Qualcomm collaborates with various institutions to advance 6G wireless communication technologies. Governments and organizations worldwide, including the Next G Alliance, are investing in 6G research and development to establish new standards and frameworks for future communication networks.
ICT Standardization Efforts
The standardization processes in the Information and Communication Technology (ICT) sector focus on the International Telecommunication Union (ITU) and its various industries, including the work of ITU-R and ITU-T, which develop recommendations for mobile communication systems from 3G to 6G.
Key organizations like the O-RAN Alliance contribute to these standards and frameworks.
Ongoing efforts aim to address security and privacy challenges associated with emerging technologies, particularly in the context of 6G.
Additionally, open research issues, such as quantum-safe encryption methods in post-quantum cryptography and enhanced network anomaly detection, require further exploration.
Conclusion
To sum up, wireless communication has evolved significantly with the emergence of 6G, enabling enhanced data speeds, near-zero latency, and increased capacity for numerous connected devices.
However, the complexity of 6G networks has introduced new challenges regarding security and privacy. Integrating various IoT devices, AI, and edge computing raised the risk of data breaches and unauthorized access, necessitating robust security measures and stringent privacy technologies.
The survey provided an overview of 6G's development, focusing on architecture, protocols, security, privacy, and standardization. It identified existing and emerging security and privacy risks, including vulnerabilities inherited from 5G and potential attacks on 6G protocols, while discussing a range of mitigation strategies and key future research directions.

 *Important notice: arXiv publishes preliminary scientific reports that are not peer-reviewed and, therefore, should not be regarded as definitive, used to guide development decisions, or treated as established information in the field of artificial intelligence research.
*Important notice: arXiv publishes preliminary scientific reports that are not peer-reviewed and, therefore, should not be regarded as definitive, used to guide development decisions, or treated as established information in the field of artificial intelligence research.
Journal reference:
- Preliminary scientific report.
Yang, M., et al. (2024). From 5G to 6G: A Survey on Security, Privacy, and Standardization Pathways. ArXiv. DOI: 10.48550/arXiv.2410.21986, https://arxiv.org/abs/2410.21986